CCC is fully qualified for use with FileVault-protected volumes (HFS+ and APFS, however note that Apple no longer supports creating HFS+ encrypted volumes on Big Sur+).
Standard Backup: Enabling encryption on a volume that will not contain an installation of macOS
If you're not creating a legacy bootable backup, and if you have no intention of installing macOS onto your backup volume, there are two simple options for encrypting the backup:
- New backup: Erase the backup volume as APFS Encrypted in Disk Utility.
- Existing backup: Right-click on the APFS-formatted volume in the Finder and choose the option to encrypt the volume. (Note: If this backup was previously part of a full system backup, Finder will fail with an "Internal error", or indicate "This disk has macOS users". If you see that message, you'll have to erase the volume as APFS Encrypted in Disk Utility instead).
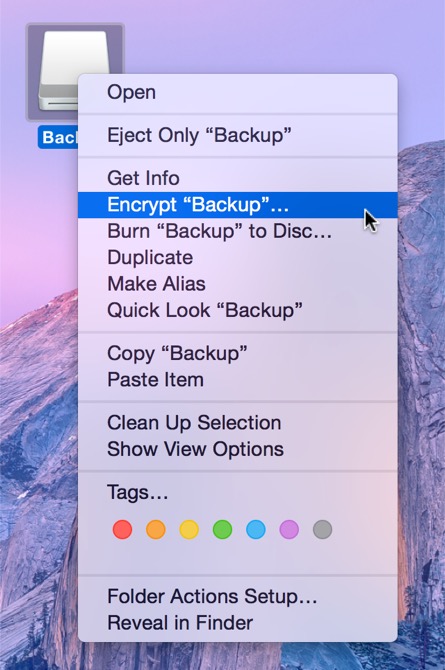
Legacy Bootable Backup: Enabling encryption on a volume that contains (or will contain) an installation of macOS
If your goal is to create a legacy bootable backup that is encrypted, use the following procedure:
- Follow CCC's documentation to properly format the destination volume. Choose APFS as the format, do not format the volume as encrypted.
- Use CCC to back up your startup disk to the unencrypted destination volume. [Big Sur (and later OS) users, use the Legacy Bootable Backup Assistant]
- Reboot your Mac while holding down the Option key (Intel Macs) or the Power key (Apple Silicon Macs) and choose your backup disk as the startup disk.
- Enable FileVault encryption in the Security & Privacy preference pane of the System Preferences application.
- As soon as the encryption conversion procedure begins, you may reboot your Mac — it will automatically reboot from the production startup disk.
- Configure CCC for regular backups to your encrypted backup volume.
You do not have to wait for the conversion process to complete before rebooting from your production startup disk
You do not have to wait for the conversion process to complete before using your backup disk. You can simply enable FileVault encryption, then immediately reboot from your primary startup disk and the conversion process will carry on in the background. Encryption will continue as long as the backup disk is attached. macOS doesn't offer a convenient method to see conversion progress, but you can type fdesetup status -device "/Volumes/CCC Backup" -extended in the Terminal application to see conversion progress. Some users have found that conversion may not resume until you log in to an admin account while booted from your production startup volume, so try that if conversion appears to be stalled.
Keep your Mac plugged into AC power for the duration of encryption conversion
We have received a handful of reports from macOS Catalina users indicating that encryption conversion remains permanently paused if AC power is removed during the encryption conversion process. We have been unable to reproduce this result in our test lab — typically encryption conversion pauses when AC power is removed, but then resumes when AC power is restored. The number of reports to us, however, suggests that there is some underlying problem that may be new to macOS Catalina. To avoid this result, we recommend that you keep your Mac plugged in to AC power for the duration of encryption conversion. If you see an indication that encryption conversion is paused, try leaving the system plugged into AC overnight.
What if I don't want my personal data to ever be on the destination in unencrypted form?
Enabling FileVault on the destination means that the volume starts out unencrypted, and then over the course of several hours the data is encrypted in place. If the encryption conversion process completes successfully, then for most intents and purposes, no trace of the unencrypted data will be left on that disk. There are some caveats however. If your backup volume is an SSD, and if you delete files from the SSD prior to enabling encryption, then the SSD may automatically move the not-yet-encrypted underlying blocks out of rotation (for wear leveling), and those data could be recoverable by experts. Likewise, if the conversion process fails for any reason, then the data on that disk is potentially recoverable. If either of these scenarios is not acceptable, then we recommend that you exclude any sensitive data from the initial backup task. Don't exclude your whole home folder — you must include at least one folder from your home directory so that you can log in to that account on the backup.
After you have booted from the backup volume and enabled FileVault, you can then reboot from the production startup disk, remove the exclusions from your backup task, then run the backup task again to copy the remainder of your data. Any data that is copied to a volume that is in the midst of encryption conversion will be encrypted immediately.
Note for Big Sur (and later OSes) users: Do not use the Legacy Bootable Backup Assistant to configure your initial backup task, you will not be able to exclude content from a Full Volume Clone. After the initial Standard Backup has completed, proceed to install macOS onto the destination. After installation has completed, enable FileVault, then reboot from your production startup disk and run your CCC backup task again without the exclusions.
Related Documentation
- Frequently Asked Questions about encrypting the backup volume
- The Disk Center
- [Apple Kbase] Learn more about FileVault
"A recovery key has been set by your company, school, or institution"
If you migrated data from a Mac that had an institutionally-managed FileVault Recovery key, the presence of that key can prevent you from enabling FileVault. You can remove that key in the Terminal application:
sudo rm -f /Library/Keychains/FileVaultMaster.cer /Library/Keychains/FileVaultMaster.keychain
sudo fdesetup removerecovery -institutional
sudo fdesetup changerecovery -personal
Then proceed with the instructions above to enable FileVault in System Preferences.
Additionally/alternatively, you can exclude the /Library/Keychains/FileVaultMaster.cer and /Library/Keychains/FileVaultMaster.keychain files from your CCC backup task to avoid copying those to your backup disk.
